Places to Check Manually
Places to Check Manually
| Quick Reference – Places to Check Manually for Malware Search these files and folders for malware: First – Select “Show hidden files, folders, or drives” |
Registry Reference Articles Windows Program Automatic Startup Locations Windows Automatic Startup Locations Top Ten Registry Launch Points |
| Regsitry Locations Reference HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion 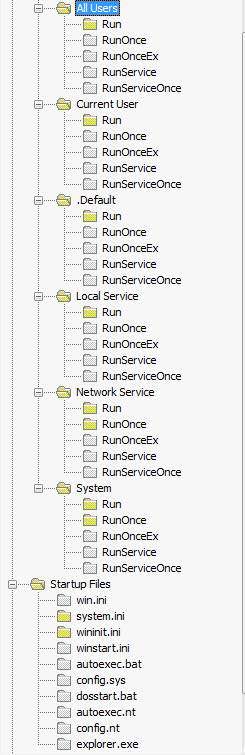 |
Breaking it down even more. These registry paths are the most common paths that malware will reside to start up with the system: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce Other places to check: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\*service* >ImagePath HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\explorer\User Shell Folders HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SharedTaskScheduler HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\ShellExecuteHooks HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Toolbar HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved HKEY_LOCAL_MACHINE\Software\CLASSES\batfile\shell\open\command HKEY_LOCAL_MACHINE\Software\CLASSES\comfile\shell\open\command HKEY_LOCAL_MACHINE\Software\CLASSES\exefile\shell\open\command HKEY_LOCAL_MACHINE\Software\CLASSES\htafile\Shell\open\Command HKEY_LOCAL_MACHINE\Software\CLASSES\piffile\shell\open\command HKEY_CLASSES_ROOT\exefile\shell\open\command HKEY_CLASSES_ROOT\comfile\shell\open\command HKEY_CLASSES_ROOT\batfile\shell\open\command HKEY_CLASSES_ROOT\htafile\Shell\Open\Command HKEY_CLASSES_ROOT\piffile\shell\open\command |
AutoStart Entry Points in Windows Explained
Following is a list of some of the more frequently used autostart entry points in Windows, including startup folders, registry keys, and ini files. Use the list as a guide as to where to look for the signs of a malware infection – but remember, registry edits and system changes should only be attempted by experienced users.
WIN.INI file
The WIN.INI file was used in earlier versions of Windows (3.x and 9x) to load applications and configuration settings at startup. Though no longer used by default on newer operating systems such as Windows XP, values included in these files will still be acted upon. Thus, some malware authors will leverage the WIN.INI file to load viruses or other malicious software. The pertinent sections to check in the WIN.INI file are the <load> and <run> lines located under the [Windows] heading.
System.ini File
The system.ini file was used in earlier versions of Windows to load device drivers and the explorer shell. The reliance on system.ini was phased out and is no longer relied upon by Windows XP and above. In the case of an upgrade from an older OS, such as 9x, to Windows XP or above, the settings contained in system.ini will be retained. Though a fresh installation of Windows XP or above will not include any data in the system.ini, subsequent inclusions will be acted upon by the OS. Hence malware authors still occasionally use the system.ini to cause viruses and other malicious software to load. The pertinent line to check in the system.ini file is <shell>, located under the [boot] heading.
Startup Folder
The Windows Startup folder can include shortcuts, documents, executable, or other types of files and programs to be launched when Windows is started. The current logged on user can view startup folder inclusions through the Start menu: Start | Programs | Startup
Items in the Startup folder can also be viewed by navigating to:
%USERPROFILE%\Start Menu\Programs\Startup (where %USERPROFILE%) signals the username of the logged on user)
The common startup folder, applicable to all users, correlates to:
%ALLUSERSPROFILE%\Start Menu\Programs\Startup
System Registry Run Keys
Certain registry keys may contain values used to load applications (including malware) when Windows is started. The values
to examine are located in sub-keys Run, RunOnce, RunServices, and RunServicesOnce, located in either of the following registry keys:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\
System Registry – Winlogon
Winlogon is responsible for supporting the DLL responsible for managing the interactive logon when Windows starts. Pre-Vista,
that DLL provides a customizable user interface and authentication process. Malware that hooks into Winlogon can be particularly
difficult to remove, as even booting into Safe Mode will not deactivate it. The string values that customize the Winlogon process
are located in the following registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows NT\CurrentVersion\Winlogon
For more information specific to Winlogon, see Winlogon and Gina – Microsoft and Winlogon – Wikipedia
ASEPS Specific to ME, 2000, XP
Users running Windows ME, 2000 or XP will also want to check the following registry keys for any unexpected values:
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
HKCU = HKEY_CURRENT_USER
HKLM = HKEY_LOCAL_MACHINE
Active Setup
The Active Setup registry key is an often overlooked load point. Programs register themselves using CLSIDs. For each CLSID listed under the
Active Setip key, look for the value “StubPath”. Any program specified by the StubPath value will be loaded when Windows is started.
Pertinent key location is:
HKLM\SOFTWARE\Microsoft\Active Setup\Installed Components\
Upgrades from Windows 9x
Users who installed an upgrade version of ME, 2000, or XP over an installation of Windows 9x will also want to check the following registry locations:
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion
These keys will contain items from the <load> and <run> lines of the win.ini file used by Windows 9x.
ASEP Loading Sequence
The order in which Windows processes the autostart entry points is as follows:
RunServices ⁄ RunServicesOnce – HKEY_LOCAL_MACHINE and HKEY_CURRENT_USER RunServices⁄RunServicesOnce will be launched concurrently.
In the event of a conflict, precedent is given to HKEY_LOCAL_MACHINE. These ASEPS may continue loading during and after the login dialog.
Login Dialog (Winlogon)
RunOnce ⁄ Run for HKEY_LOCAL_MACHINE hive
Run key in HKEY_CURRENT_USER hive
Startup Folder
RunOnce in HKEY_CURRENT_USER hive